Scan for misconfigurations in laC templates. Auto-remediate at the source with a pull request
laC scanning (Terraform, Helm, Kustomize)
Auto-Remediation
Detect threats based on Falco. Conduct forensics even after the container is gone
syscall detection
Kube-API detection
Activity audit
CloudTrail detection
Network security
Captures
%20(1).png)
Scan for vulnerabilities and misconfigurations across containers and hosts
CI/CD registry
Runtime scanning
Host scanning
Manage cloud posture. Enforce compliance & governance in K8s based on OPA
CIS benchmarks
Compliance frameworks
Policy as code
You can manage risk when configuring cloud infrastructure & shift security further left with Infrastructure as code (IaC) security.
Open Policy Agent (OPA) allows you to strengthen cloud and Kubernetes security, and compliance, by using policy as code.
Sysdig Scure allow you to gain consistent visibility of cloud security risk by flagging misconfigurations and suspicious activity.
You can now unify cloud security posture management (CSPM) and cloud threat detection.
You can now gain visibility into cloud identities and their permissions to access resources using a CIEM tool like Sysdig Secure.
Sysdig allows you to meet regulatory compliance standards for containers and cloud wth ease.
Save time with out-of-the-box policies that map to specific compliance controls and implement File Integrity Monitoring (FIM).
You can now automate CI/CD pipeline and registry scanning without images leaving your environment. At the same time, block vulnerabilities pre-production and monitor for new CVEs at runtime for containers and hosts.
Sysdig also automatically prioritize vulnerabilities based on runtime context, and map critical vulnerabilities for you
Sysdig allows you to secure containers, CaaS (AWS Fargate), Kubernetes, hosts and cloud infrastructure with out-of-the-box policies based on open source Falco.
Sysdig supports a Zero Trust approach to container network security by allowing only required communication.
You can now Visualize all network communication between pods, services, and applications inside Kubernetes.
Use Sysdig secure to conduct forensics and incident response for containers and Kubernetes to understand security breaches, meet compliance requirements and recover quickly.
Facilitates Incident response and container forensics for Kubernetes.
2020 saw an acceleration of cloud adoption that led to an increase in container usage. This increase, combined with the fact that half of containers live less than 5 minutes, reinforces the need to manage container-specific security risks. A majority of our customers scan images during the build stages, but we still see risky configurations. To run container applications with confidence, it’s important to address configuration risk, detect runtime threats, and ensure that a detailed recording of container activity is available for incident response and forensics. As we have done the past four years, we are sharing critical annual insights from real-time, real-world usage of nearly 1 billion unique containers that our customers have been running in our environment over the past year. Our goal is to shed light on the current state of container infrastructure, applications, security, and compliance practices.
of customers are scanning images duringthe CI/CD build stage
of containersrun as root
of containers liveless than 5 minutes
increase inFalco adoption

growth of Prometheusmetric use

increase inusage of Go

As Kubernetes scales up, security is the #1 challenge facing DevOps according to IDC Tech Brief
52% container images fail scans with high severity* that leaves applications exposed to attacks*
On average, 21 containers per node are running as root, opening the door for container breakouts*
5 min container lifespan requires purpose-built tools for audit and incident response*
.png)
Maximize application availability
Sysdig Monitor collects metrics about your environment from our eBPF based agent, Kubernetes, Prometheus, integrations, cloud services, and custom metrics. We then correlate and enrich those metrics so you can get maximum visibility to ensure application availability, performance, and fast problem resolution. With a prioritized list of issues, out-of-the-box dashboards, easy-to-use alerts, and simple integrations you can start quickly and scale simply to get more done.
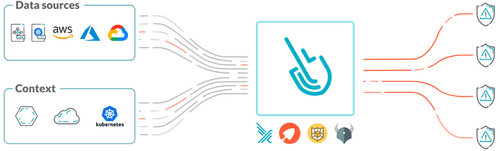
Easily Integrate with other tools you use. Detect anomalies based on Falco, the cloud native standard for threat detection. Enforce consistent policies based on OPA, the cloud native standard for configurations. Maximize coverage with community-sourced detection rules that are easily customizable.

Falco is the open standard for runtime security.

The Open Policy Agent is an open source policy engine that unifies policy enforcement across the stack.

Cloud Custodian is an open-source rules engine for cloud configuration management.

Sysdig OSS is the standard for cloud and container forensics.
Get unified visibility across workloads and cloud infrastructure from a single cloud security and monitoring platform. Accurately alert on threats, operational issues and compliance risks and respond using a detailed activity record. Easily plug into your existing workflows with out-of-the-box integrations.
Single agent for hosts, containers, and Kubernetes. Continuous cloud security running locally in your account.
No infrastructure to manage. Scale quickly as your environment grows.
Save time with out-of-the-box dashboards and curated policies powered by the community.